We understand your concerns regarding the security of your account and your data.
As per our privacy policy, we do send mobile notifications, marketing emails, newsletters, and invitations to our users to promote our services and free content (i.e., webinars and video series) but if you prefer not to receive any of those, you can always let us know and we will humbly unsubscribe your account so that you will not receive those kinds of promotions.
If you engage our parent company, Empower Wealth for their financial services such as mortgage broking, financial planning and tax accounting, we may disclose your personal information to prospective funders/lenders, lenders mortgage insurers, the ATO and credit reporting bodies or other intermediaries to ensure that we can deliver on our services.
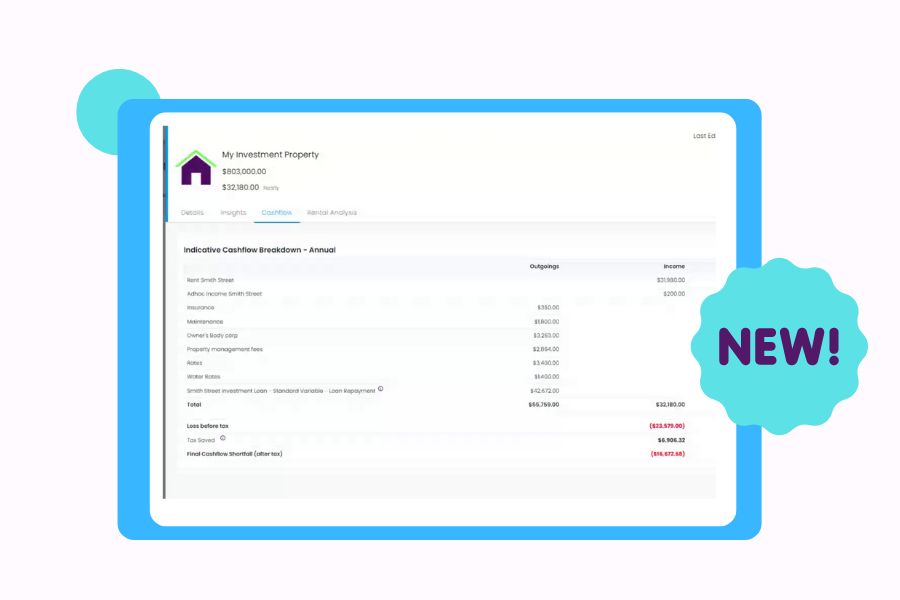
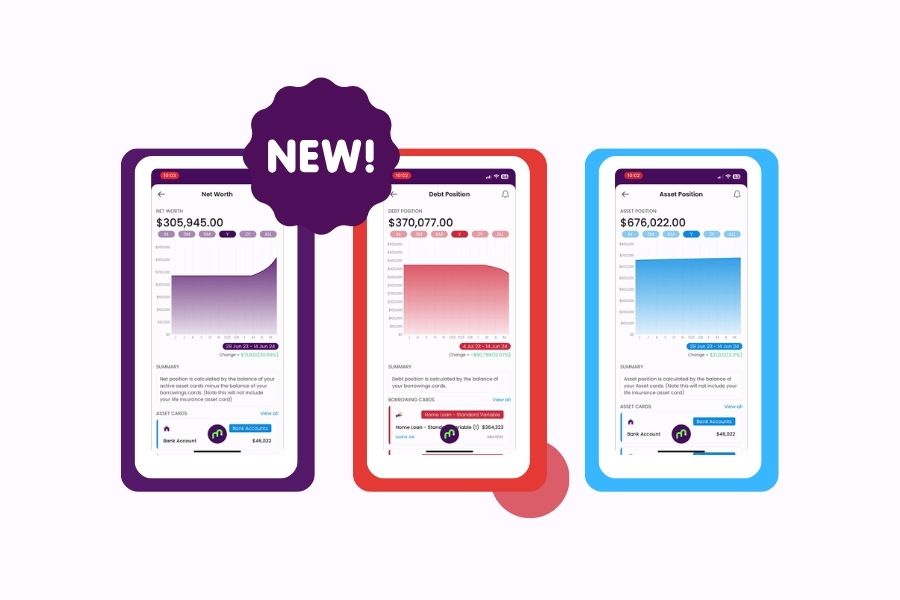
In regards to your concern about security, the portal is secured with two options of 2-factor authentication to make sure that you and an authorized user can access your account securely. We currently employ Google Authenticator as well as an SMS authenticator to make sure that you can only log in to your account from a verified device and remove the risk of your account being hacked especially since you may have some sensitive information saved there.
Once again, I’d like to emphasize that we, at Moorr, value our customer’s right to data privacy and we will continue to take all measures to protect and secure your account. Any changes that need to be done to your account will be only done with your consent and you can always opt-out from receiving any marketing notifications from us by letting us know through this link: https://www.moorr.com.au/support.
👉 Take charge of your financial future with Moorr’s innovative platform! Get it here for Apple devices and for Android devices, click here, for seamless security and strategic insights.